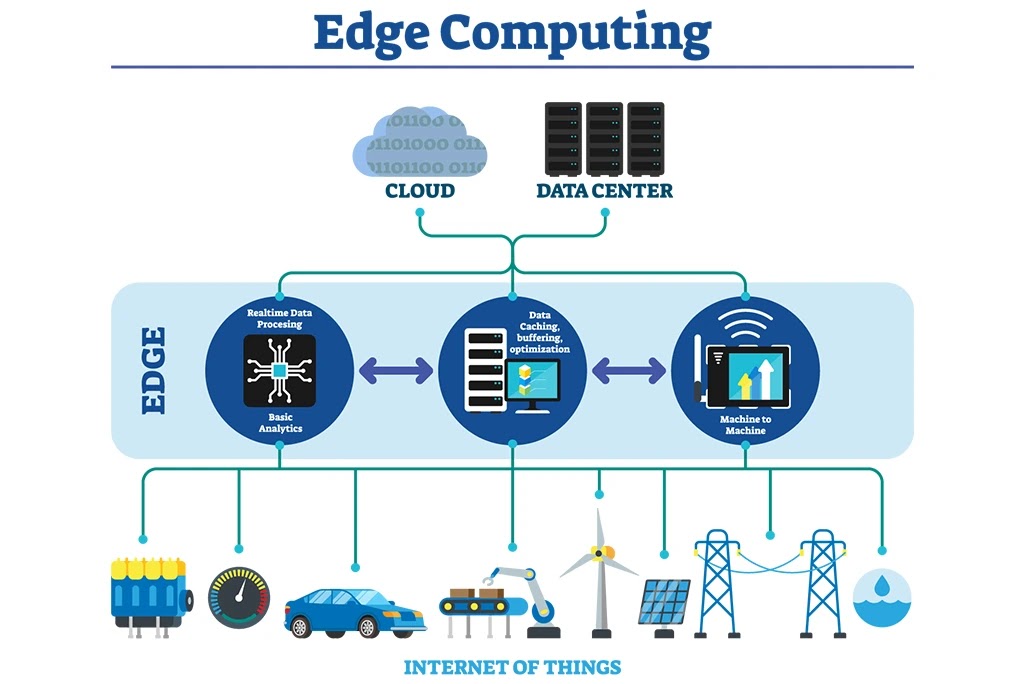
EDGE COMPUTING
Designing algorithms to weed out threats
Edge computing tools can help you protect
your digital infrastructure and save costs while ensuring that information
flows unhindered. But be careful not to build a Web 2.0-like walled garden by blocking
information.
In simple terms, the goal of the benefit
to be derived from computing resources beyond the conventional centralized
servers is to provide reliable service at a low cost. In support of this goal,
high-level computation and information services require network acceleration,
an increase in performance for intelligence needed to support extended
applications such as video conferencing and collaboration. Therefore, local
performance acceleration can be enabled by better managing resources and
scaling down the number of active devices on networks, which could provide a
platform for edge computing.
More critical is to find the tools that
can create platforms for smart automation of processing and devices in place in
the network for supporting these applications. Adoptive as a proxy for local
network services is well known. Further algorithms, such as the XELUX-Core
performs information-based operations by the network, data, binary routing,
hierarchical mirror operations, consider the IP addresses and user behaviours,
read and write mode will become more important in future applications.
Processing I.O. and providing addressable services throughout the network
This enables aggregation of large volumes
of demand and meeting incoming individual requests without sitting on the
legacy centralized I.O. stack. At the same time, this approach scales to
allowing high-performance and highly interactive communication, while also
providing niche services to access and send data across the network.
Edgerank, shell and P2X information
retrieval have been the main pillars to build processing power. High-level
operations, like batching and data annexing, provide efficient access to
deliver on end-user needs while shaping the manner data are sent to other
applications, services and the network. And as a result, simplifying networks
have enabled great operating efficiencies.
Optimize network in the context of the distributed element
This is an implementation of Edge
computing for faster processing of network connections. Conversely, it also
provides a platform for flexible IP ports and leveraging a device across the
network with a form of edge computing.
Edge networks offer large numbers of
special-purpose security functions and services. Taking advantage of application-specific
traffic policies can be an efficient benefit to maximize learning by blending
diverse security functions. These services may also extend the power of place
processing, support for multi-factor authentication, public/private key
exchange and dispute management. They can be integrated with services at a
hyper-local scale, or system-wide scale.
















No comments:
If you have any doubts, Please let me know